Running as the Admin user on your system means that things that happen to you are not isolated!


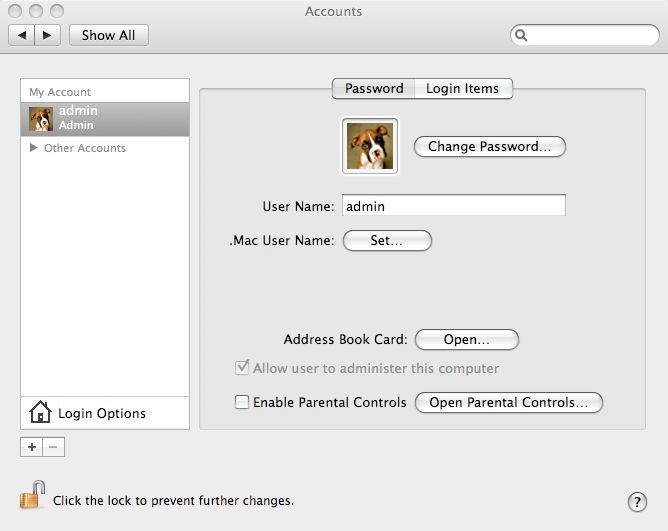
Of course the problem is as soon as you set up your mac, you have set it up that exact way. This is why it helps to know in advance to not bother naming the first account after yourself. You will be the second account created.
If you were not so lucky and have already set up your mac, then START OVER!, No, just kidding. You can cadd an account anytime by pressing the Plus icon at the bottom of the accounts system preference pane.
ß
I am looking for the images of the initial setup assistant to help. They will go here along with more snaps of the process.
The image above is from a good reference on accounts hosted by MacVsWindows. Check it out!
Operating the system with elevated privileges on a regular or constant basis opens the attack surface of the system considerably. If you get a bad email or hit a compromised site, your advanced privileges will give the attacker greater access to the system. Operating as a lowly standard user makes this more difficult. A standard user would be confronted by a barrage of unsolicited requests for administrative credentials. When the user does not posses the necessary user name and password, the attack is thwarted. Even when the user does posses the administrative account information, it may be just enough to give the user pause, to make the user question the process underway, to make the user stop, and maybe consult a friend or associate, or the service in question. Most things a user will have to do in daily operations can be done with their standard account password. Admin credentials are not required. A Trojan Horse will help illustrate the problem.
“Trojan horses are designed to allow a Hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system, it is possible for a hacker to access it remotely and perform various operations. The operations that a hacker can perform are limited by user privileges on the target computer system and the design of the Trojan horse.”
Since a Trojan succeeds because the user has advanced administrative priviledges, it makes sense to have the user operate with a standard, non-priviledged account.
©℗ 1986-2015 Silence. All rights reserved. Registered trade and service marks are the property of their holders, may not be reproduced without the holders express permission and are used by permission or as editorial content and for review.